It began with a harmless email. Employees received a message from a trusted supplier to update their email credentials “for security compliance.” Everything looked legitimate: the logo, the tone, even the signature. Except it was not from the supplier.
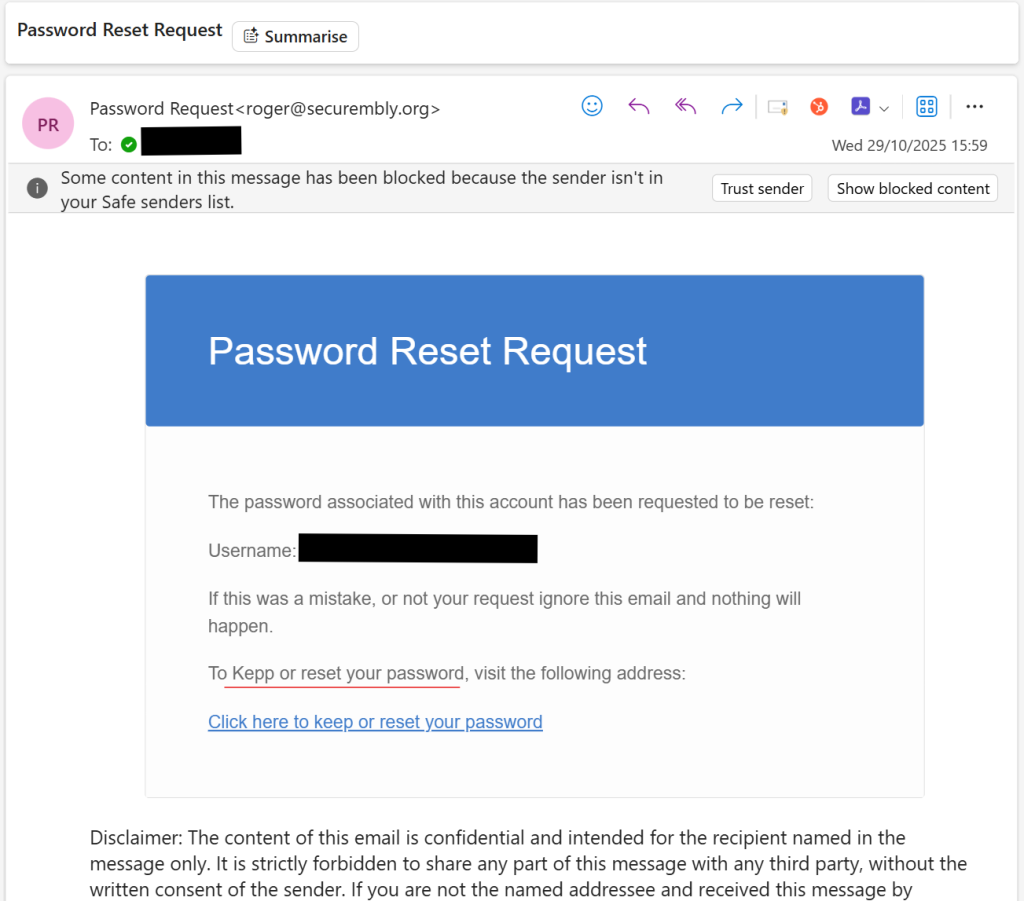
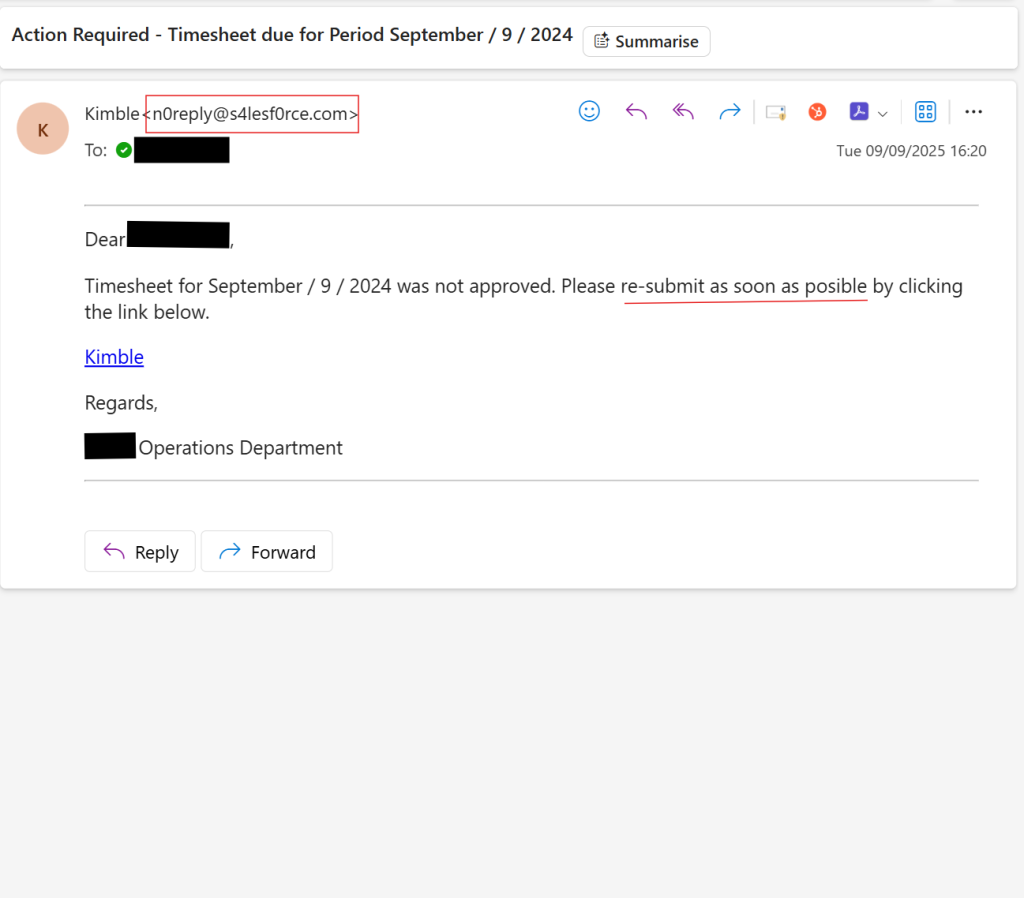
It was a targeted phishing campaign, designed to take advantage of new joiners who were still getting used to company systems and processes. The timing was perfect. Employees in the middle of onboarding process, responding to multiple IT requests. A few clicked unknowingly, getting their credentials compromised. And before long, the attackers were using those same accounts to spread further within the organisation.
When the business reached out to 3B Data Security (3BDS), our team immediately mobilised. Within hours, we had isolated the affected accounts, blocked malicious domains, and traced the attack’s path. Collaborating with the client’s internal IT and leadership teams, we restored control, analysed the incident, and strengthened their defences so it wouldn’t happen again.
Incidents like these which are fast-moving, human-led, and often preventable are becoming increasingly common. Over the years, we have helped countless organisations face similar challenges. And while every case is different, we have noticed the same obstacles come up time and again.
The Challenges We See Most Often
1. Unclear Escalation Paths
In the chaos of a live cyber incident, every minute matters. Yet, many teams lose precious time figuring out who’s in charge, what to escalate, and when. Those moments of hesitation can turn a small problem into a widespread crisis.
We’ve seen it happen:
In one case, a simple alert sat unaddressed for hours because no one knew who was responsible for triggering the response plan. By the time action was taken, the infection had spread across key systems.
How to fix it:
Define your escalation process clearly and make it second nature.
Everyone, from front-line IT staff to executives, should know who to contact and what their role is. Regular tabletop exercises are the best way to make sure theory translates into action.
2. Gaps in Visibility
You cannot defend what you cannot see. Many organisations still struggle to get a complete picture of what is happening across their networks, endpoints, and cloud environments. That lack of visibility makes it hard to detect threats early or understand how far they have spread.
We’ve seen this first-hand:
A client’s investigation into a data breach stalled because their monitoring tools were not integrated across environments. They had the right data, but it lived in silos.
How to fix it:
Invest in centralised threat monitoring that unifies visibility across all platforms.
Regularly test your detection coverage to make sure there are no blind spots. The sooner you can see a problem, the faster you can contain it.
3. Communication Breakdowns
Even the best technical teams can stumble when communication falters. During a cyber incident, leadership needs clear, jargon-free updates to make informed decisions while technical teams need space to act fast without getting lost in red tape.
We’ve seen what happens when that balance breaks down:
Inconsistent updates, conflicting messages, and sometimes even unnecessary public confusion.
How to fix it:
Build communication into your response plan.
Assign a spokesperson, define update intervals, and ensure executives get the right level of detail. Not too little, not too much. Clarity and calm communication can make or break your response.
4. Limited Post-Incident Analysis
Once the crisis is over, it’s tempting to move on. But skipping the debrief means missing vital lessons. Every cyber incident, big or small, offers insights that can strengthen your defences for the future.
We’ve seen it too often:
A company resolves a phishing attack but doesn’t update training or review policies. Months later, a similar attack succeeds exploiting the same gap.
How to fix it:
Make post-incident reviews part of your culture.
Analyse what went well, what didn’t, and how to improve. Feed those insights into training, policies, and processes. That’s how you turn incidents into opportunities.
From Reaction to Readiness
At 3B Data Security, we believe that resilience is built long before an incident happens. Our work isn’t just to contain vulnerabilities. It’s to help organisations prepare, respond, and recover with confidence.
By putting structure, communication, and learning at the heart of every response plan, we help teams move from panic to precision and from reaction to readiness.
If you’d like to understand how your organisation would handle a real-world incident or how to strengthen your response framework, let’s talk.
Schedule a call with our team to discuss your incident response readiness.
Because when every minute counts, preparation isn’t optional, it’s everything.






