“By failing to prepare, you are preparing to fail.” Benjamin Franklin’s words hold true for every crisis scenario. When people face an emergency without prior practice – like a fire – they often panic, take the wrong actions, or freeze altogether. But those who have gone through fire drills know exactly what to do. Preparedness turns confusion into calmness, and hesitation into decisive action.
Cyber incidents are no different. Awareness, rehearsal, and clear response patterns determine whether an organisation contains an attack or watches it spiral out of control.
With that in mind, our cybersecurity expert, Andrew Bassi – offers insights into why traditional approaches need to evolve and how Cyber Incident Exercising is shaping modern readiness.
The Vantage Point – Andrew Bassi – The Death of the Tabletop Exercise
Until recently, tabletop cyber security exercises were a staple of any serious approach to maintaining and improving an organisation’s security posture. Tabletop exercises engage key stakeholders within the organisation such as senior management, IT and SOC teams, HR, PR and legal staff. Through a series of roleplay-based exercises (usually called injects) the stakeholders are encouraged to walk through the incident response plan and discuss where potential issues may arise.
The value of tabletop exercises should not be overlooked; they allow the organisation to test potentially business crippling scenarios without having to wait for the scenario to manifest in real life. A good tabletop exercise will test the response of the organisation in several different ways to tease out any gaps in processes, people or technologies. Lessons learned from the tabletop are fed back into the Incident Response plan (like when a real incident is dealt with).
However, they do come with some drawbacks.
- The first of these is the ‘roleplay’ nature of the delivery. This makes it hard to create realistic scenarios without a lot of research into the systems and processes an organisation already has. In turn, the delivery of the exercise is ‘contrived’ and fails to engage people in the necessary way.
- The next drawback is that because the scenarios are entirely theoretical, no testing of the infrastructure is performed.
- Another drawback is that they follow a static flow instead of changing and responding to the performance of the team, this can lead to scenarios that do not make logical sense (i.e. a step taken by the team on one inject completely negates the next inject).
So, what is the solution to these issues?
Introducing Cyber Incident Exercise.
Cyber Incident Exercises (CIE) aim to build upon the tabletop exercise rather than replace it completely. The key stakeholders from all parts of the organisation are still present and there are still scenarios which are played out. It is how the scenarios are played out that is different.
In CIE, the scenarios are played out using either a simulation or live tools. A manual example would be dropping a known malicious file (usually an EICAR file which is automatically detected as a virus despite being just a plain text file) on a server or workstation in the network. This will trigger the in-place Antivirus or Endpoint Protection and the alert generated should prompt SOC and first responders to enact the incident response process.
Where CIE can really excel is in emulating real world adversaries and the types of attacks they employ. To do this effectively, it’s useful to have a framework that describes these attacks and allows the consultant to string these attacks together into something similar to that seen when an Advanced Persistent Threat or even a disgruntled employee attacks the system. A common framework when classifying attack methods is MITRE att&ck framework.
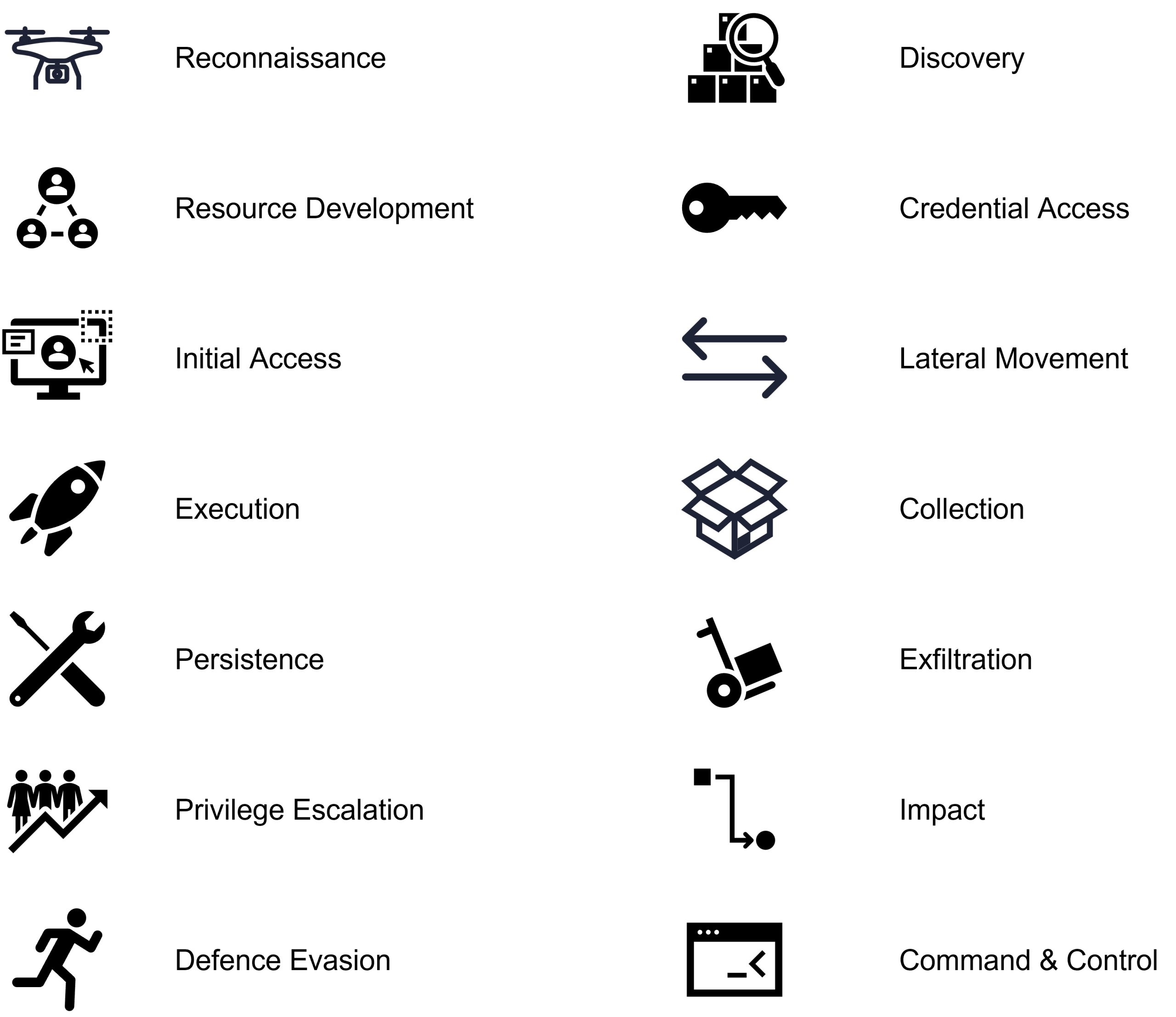
To deliver CIE engagements, 3B Data Security deploy an agent on systems in the target network (this can be a test network or production). This agent can in turn emulate thousands of potential MITRE att&ck code snippets which will test and trigger end point detection technologies. Using a library of pre-configured ‘atomics’, the consultant can build out an attacker profile. This profile can then be pushed out to the agents in the network to test the technology, the response of the teams to the events that are generated will test the process and people aspects.

From Hypothetical to Practical: Why CIE Enhances Tabletop Exercises
As stated before, CIE attempts to build on tabletop exercises rather than replace them. This allows for input from senior managers, legal, PR and HR teams to influence and question the approach taken by the organisation as a whole. The live-play elements introduced in CIE serve to bolster the realism of the scenarios as well as test the technology, process and staff.
Another advantage of CIE is that due to the structured nature of the live-play elements, it is much easier to quantify the organisations response. Whereas previously under tabletop exercises there was a subjective nature to feedback, it is now possible to score the response based upon the performance during the live play.
For clients wary to test against their production or test networks, it is possible to deploy a CIE agent to a standalone machine that is representative of the target machine type in the organisations network (i.e. a server). This can be a virtual or actual machine. This however does not benefit from the real-world scenario testing that a full deployment would.
In conclusion, CIE offers the best elements of tabletop with the real-world scenario testing akin to that of red team exercises. It tests not only the staff and processes, but the deployed technologies and 3rd party vendors like SOCs. It provides a structured way to test and score the organisations response rather than just the subjective feedback of a tabletop. CIE is more than a tabletop in many ways, most importantly it provides some confidence that the processes and tools can defend the organisation in the event of a Cyber Incident.
Who is Andrew Bassi
Andrew Bassi is an experienced Incident Responder and Principal IR Consultant at3B Data Security Pen Test Partners, with over a decade of expertise in Payment Card Forensics, incident response, and PCI compliance. He has audited organisations of all sizes and delivered forensic work across leading security firms.. He has presented at major industry events, including the European PCI Community Meeting, and brings deep operational insight from his earlier career at SunGard and academic grounding from a master’s in information security at Royal Holloway.
More About CIE
The expert insights above highlight a fundamental truth: modern attacks outpace traditional rehearsals. Cyber Incident Exercising evolves the tabletop approach by introducing realism, live triggers, and measurable performance.
CIE Brings Several Critical Advantages:
1. Realistic Technical Stimuli
Instead of discussing hypothetical alerts, CIE generates real ones, forcing SOC teams to detect, triage, and respond.
2. Adversary Emulation with MITRE ATT&CK
CIE leverages structured attack behaviours to replicate real threat actor tactics, techniques, and procedures (TTPs).
3. Operational Pressure Testing
Teams face time-sensitive decisions, tool overload, and incomplete information, mirroring an actual breach.
4. Cross-Functional Engagement
Legal, HR, PR, IT, and leadership must coordinate responses to avoid conflicting actions.
5. Quantifiable Outcomes
Unlike subjective tabletop scoring, CIE measures:
- Detection speed
- Response accuracy
- Escalation behaviour
- Containment effectiveness
It’s no longer guesswork, it’s evidence.
Preparedness: Why It Matters More Than Ever
Just as fire drills reduce panic, CIE reduces the chaos surrounding a cyber breach. Preparedness ensures:
- Teams take the right actions in the right order
- Alerts are not ignored or misinterpreted
- Leadership knows exactly when to step in
- Communications stay controlled
- Business impact is minimised
In a crisis, clarity saves minutes and minutes save organisations.
Real-World Attack Scenarios CIE Can Simulate
Social Engineering / Human-Focused Tests
- Supplier impersonation phishing
- CEO fraud requesting urgent payments
- Credential harvesting via fake login pages
- Malicious attachments with macro payloads
- Helpdesk social engineering to reset MFA
Technical Attack Path Scenarios
- Dropping EICAR test files
- PowerShell-based malicious commands
- Lateral movement attempts
- Credential dumping
- Privilege escalation
- Data exfiltration simulations
These scenarios validate the entire defence stack – people, process, and technology.
Case Studies: What CIE Reveals in Real Organisations
Case Study 1 – Ransomware Simulation Exposes Detection & Workflow Gaps
A full-scale ransomware simulation highlighted weaknesses in an organisation’s SOC workflow, cloud monitoring, and network segmentation. Although backups were robust, alert routing and detection logic failed to identify the attack early. After the exercise, processes were tightened and tooling was reconfigured to close the gaps.
🔗 Source: SafeNet Red/Blue Team Ransomware Simulation
Case Study 2 – National Cyber Simulation Reveals Escalation & Coordination Issues
A national-level ransomware simulation, run by INCIBE, demonstrated that even well-resourced teams can struggle with escalation paths, communication flow, and coordination during a live incident. The exercise prompted updates to incident response procedures and more clearly defined responsibilities across stakeholders.
🔗 Source: CSO Online – INCIBE Ransomware Simulation
Case Study 3 – Lateral Movement Blind Spots Found in Realistic Attack Modelling
Research into lateral movement detection (Hopper model) showed that internal login behaviours mimicking attacker movement frequently went unnoticed by enterprise monitoring tools. A CIE or red-team exercise using similar behaviour would reveal these blind spots, allowing organisations to improve logging, tuning, and EDR/SIEM rules.
🔗 Source: “Hopper: Modelling and Detecting Lateral Movement” (ArXiv)
How 3B Data Security Can Help
We specialise in delivering high-fidelity, adversary-aligned Cyber Incident Exercises. Our approach ensures not only that teams understand how to respond, but that systems, tools, and providers are validated under realistic load.
3B Data Security CIE Capabilities Include:
- Agent-based simulation using MITRE ATT&CK atomics
- Live-play adversary emulation
- Full organisational engagement (SOC, IT, HR, PR, Legal, Leadership)
- Measurable scoring and maturity benchmarking
- Post-exercise reporting and remediation roadmap
- Tabletop-to-CIE progression pathways
Why Organisations Trust 3B Data Security
- Deep IR expertise
- Real-world breach experience
- Operationally grounded exercises
- Clear, actionable recommendations
- Proven results across multiple industries
3B Data Security doesn’t just test readiness, they improve it.
Final Thoughts
Cybersecurity preparedness is no longer optional. Tabletop exercises alone won’t reflect the complexity and speed of today’s threat actors. Cyber Incident Exercising gives organisations the ability to rehearse, refine, and validate their defences under realistic pressure.
The best time to prepare is before the incident, not during it.
Ready to understand how your organisation would really perform during a cyber-attack?






